
How Much Do You Know About Third-Party Vendor Security?
How Much Do You Know About Third-Party Vendor Security?
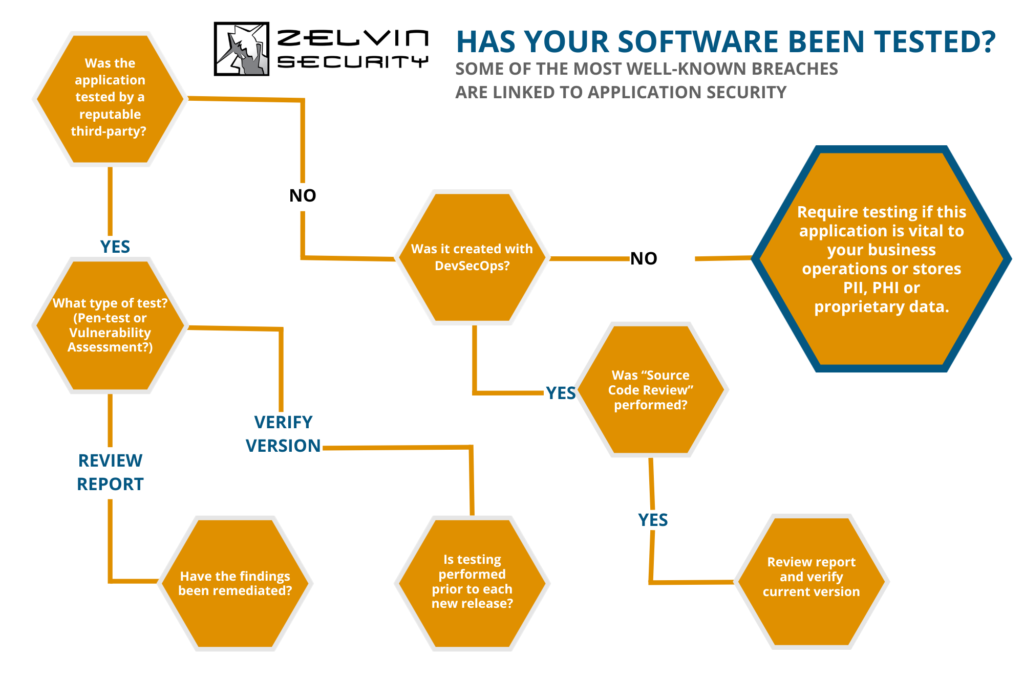
Software test flowchart included at the bottom!
In today’s digital age, businesses rely heavily on vendors to keep operations running smoothly and provide essential services. Though relieving operational burdens, this dependency on third-party vendors comes with a significant cybersecurity risk that is often underestimated. We’re going to clear up some of the misconceptions around vendor-related cyber threats and discuss strategies to mitigate them effectively.
Not sure what qualifies as a vendor? A few common examples are Microsoft Office, Google Cloud, Dropbox, payment processors, website hosts, CRMs, and the list goes on. If your business has an online component, you most likely use several vendors to get your job done!
But why are third-party vendors risky?
These partnerships, while essential for business growth, can become a pipeline for malicious actors seeking to infiltrate your network and steal sensitive client data.
Vendors are not likely to be the hackers themselves, but the potential for reputation-damaging breaches through the vendors are real. According to the Verizon Data Breach Investigations Report, nearly 45% of malicious action is “use of stolen credentials.”
Are you or your coworkers using a similar password for all accounts? Do any of your vendors’ employees reuse passwords? You can’t know for sure unless you verify their cybersecurity measures.
Here are 5 recent examples of third-party breaches so that you can understand the types of information hackers seek out in varying industries, and how the vendor was exploited.
Let’s define types of vendors so you can map out cyber risks more clearly!
- Vendors that connect to your network and access client data – These vendors have direct access to your network and may handle critical client data. Any breach on their end could lead to a devastating data compromise for your organization.
- Vendors who give you the supplies or ability to serve clients – These vendors provide the materials, tools, or services that enable your business to serve your customers. While they might not have direct network access, a compromise on their end could still lead to an attack on the confidentiality, integrity, or availability of critical business processes.
Do your Due Diligence!
To protect your organization from vendor-related cyber risks, it’s a good idea to have an established process for onboarding and offboarding.
- For onboarding – Implement a thorough vetting process before bringing vendors on board. Verify they adhere to cybersecurity best practices and have measures in place to avoid breaches.
- For offboarding – It is equally important to follow a structured process to revoke access, remove vendor-related data, and make sure there are no vulnerabilities lingering around.
So, what does onboarding a Web Application Vendor look like?
- Require a letter of attestation: this document outlines their commitment to cybersecurity practices, including regular security assessments and compliance with industry standards.
- Test the web application annually: Ensure the web application undergoes regular security testing at least annually. Types of tests available are vulnerability assessments, penetration testing, and code reviews. (And don’t just test something for compliance’ sake, but actually test the security controls.)
- Test the web application when major changes are made: Also consider performing security tests when considerable changes occur around the application.
In this scenario, we see how a weak third-party vendor can compromise the sales and reputation of an organization.
Your online store has been in business for 3 years and is wildly successful in several countries after putting so much time and resources into building the business. Your website allows customers to select products, add them to their cart, and proceed to checkout.
Problem: Your website hosting application hasn’t had a security test since you opened. One day, a customer reports a strange issue – an increase in fraudulent credit card charges after making a purchase on your site.
As you investigate, you realize that the web application has been compromised.
Upon closer examination by cybersecurity contractor, you discover a vulnerability in the websites payment processing system, allowing cybercriminals to inject malicious code, stealing sensitive customer payment information during checkout.
Not only did this breach cause financial loss for your customers but has damaged your reputation and trust of customers.
Solution: To prevent this situation, regular security testing could have identified and patched the security flaw before it was exploited by cybercriminals. This proactive approach could have protected customers and the future of your business.
Think about how this scenario parallels the threats within your industry. Do you keep all of your client files in a CRM software? What happens if your network is shut down for one business day? 3 business days?
Vendors are not just partners, but a potential gateway for cyberthreats. By knowing the risks, implementing a process to deal with them, and using a structured onboarding/offboarding process, you can better protect your organization from catastrophe.
Refer to the flow chart below to determine the next step in testing your software. Not in charge of software? Pass this article along to an IT expert in your organization!
This blog was reviewed by Matt Perrotti, a Senior Penetration Tester at Zelvin Security with 20 years of experience as an IT professional in various cybersecurity roles.
For additional education on cybersecurity, check out our event page for monthly webinars!
In the diverse landscape of cybersecurity, two distinct yet collaborative providers play pivotal roles in defending your digital space: IT Providers and Ethical Hackers. While their ultimate goal is to enhance the security posture of organizations, they approach the task…
More digital tools = more cyber risks. Does your organization use technology? Do you store client, employee, and confidential data? Few can say no, as business are efficiently scaled using digital tools to automate operations, store data, and communicate internally…
The 7 important cybersecurity strategies you can implement TODAY to help protect your network against malicious hackers. There were 28,775 known vulnerabilities in 2023, which is the highest ever recorded by National Institute of Standards and Technology in the National…
39 Cybersecurity experts, including Zelvin Security’s President, Jeff Atkinson, took to LinkedIn to address the effectiveness of vulnerability scanners to proactively protect your network. What is a vulnerability scanner? These are software applications that scan a network for known vulnerabilities….
K-12 Education Cybersecurity is increasingly more important for school district officials. Security is worth the investment.
As a proud supporter of the East Tennessee Economic Council (ETEC) community, Zelvin Security presents the following information as a guide to improve the cybersecurity programs of ETEC member organizations. One of the challenges all business leaders face is finding…
These are the core values that guide the daily work of Zelvin Security, a cybersecurity consulting firm.
Because securing digital assets is as important as locking an office door. Cybersecurity isn’t just a “nice-to-have" - It’s a must to keep your financial health and reputation intact.
Strengthen the cybersecurity of third-party vendors to enhance your organizations security posture. Use the resources in this article as a starting point to implement proactive measures.
How to Efficiently Allocate Cybersecurity Funds The economy has become more reliant on digital assets than ever before. Cybercrime is at its highest. The cost and consequences of data breaches are on the rise. This means we have to…










