
How Much Do You Know About Third-Party Vendor Security?
How Much Do You Know About Third-Party Vendor Security?
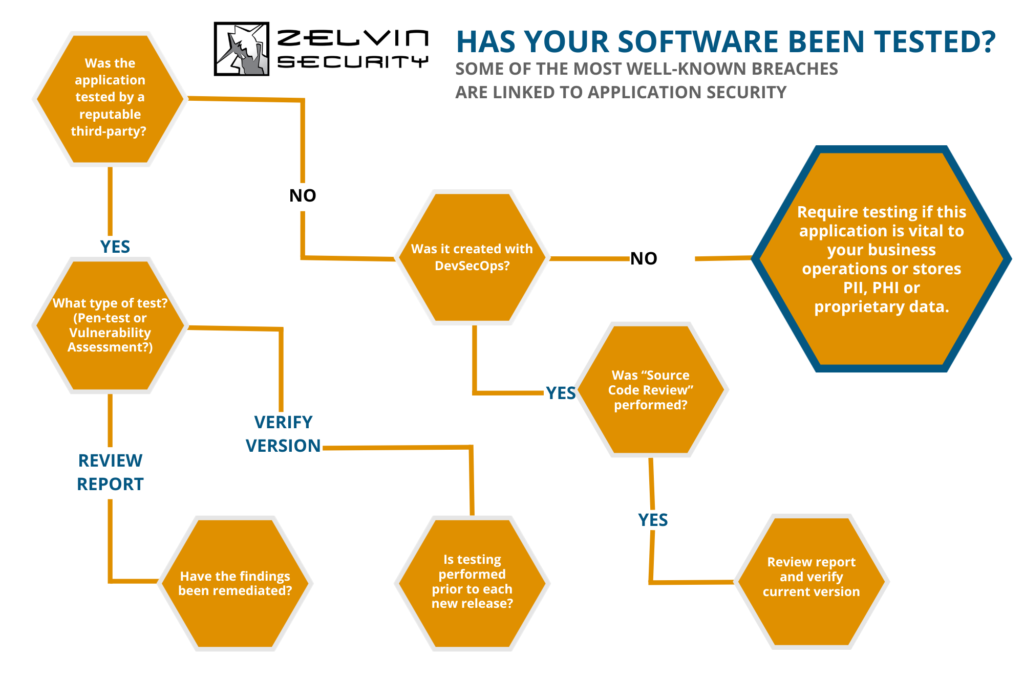
Software test flowchart included at the bottom!
In today’s digital age, businesses rely heavily on vendors to keep operations running smoothly and provide essential services. Though relieving operational burdens, this dependency on third-party vendors comes with a significant cybersecurity risk that is often underestimated. We’re going to clear up some of the misconceptions around vendor-related cyber threats and discuss strategies to mitigate them effectively.
Not sure what qualifies as a vendor? A few common examples are Microsoft Office, Google Cloud, Dropbox, payment processors, website hosts, CRMs, and the list goes on. If your business has an online component, you most likely use several vendors to get your job done!
But why are third-party vendors risky?
These partnerships, while essential for business growth, can become a pipeline for malicious actors seeking to infiltrate your network and steal sensitive client data.
Vendors are not likely to be the hackers themselves, but the potential for reputation-damaging breaches through the vendors are real. According to the Verizon Data Breach Investigations Report, nearly 45% of malicious action is “use of stolen credentials.”
Are you or your coworkers using a similar password for all accounts? Do any of your vendors’ employees reuse passwords? You can’t know for sure unless you verify their cybersecurity measures.
Here are 5 recent examples of third-party breaches so that you can understand the types of information hackers seek out in varying industries, and how the vendor was exploited.
Let’s define types of vendors so you can map out cyber risks more clearly!
- Vendors that connect to your network and access client data – These vendors have direct access to your network and may handle critical client data. Any breach on their end could lead to a devastating data compromise for your organization.
- Vendors who give you the supplies or ability to serve clients – These vendors provide the materials, tools, or services that enable your business to serve your customers. While they might not have direct network access, a compromise on their end could still lead to an attack on the confidentiality, integrity, or availability of critical business processes.
Do your Due Diligence!
To protect your organization from vendor-related cyber risks, it’s a good idea to have an established process for onboarding and offboarding.
- For onboarding – Implement a thorough vetting process before bringing vendors on board. Verify they adhere to cybersecurity best practices and have measures in place to avoid breaches.
- For offboarding – It is equally important to follow a structured process to revoke access, remove vendor-related data, and make sure there are no vulnerabilities lingering around.
So, what does onboarding a Web Application Vendor look like?
- Require a letter of attestation: this document outlines their commitment to cybersecurity practices, including regular security assessments and compliance with industry standards.
- Test the web application annually: Ensure the web application undergoes regular security testing at least annually. Types of tests available are vulnerability assessments, penetration testing, and code reviews. (And don’t just test something for compliance’ sake, but actually test the security controls.)
- Test the web application when major changes are made: Also consider performing security tests when considerable changes occur around the application.
In this scenario, we see how a weak third-party vendor can compromise the sales and reputation of an organization.
Your online store has been in business for 3 years and is wildly successful in several countries after putting so much time and resources into building the business. Your website allows customers to select products, add them to their cart, and proceed to checkout.
Problem: Your website hosting application hasn’t had a security test since you opened. One day, a customer reports a strange issue – an increase in fraudulent credit card charges after making a purchase on your site.
As you investigate, you realize that the web application has been compromised.
Upon closer examination by cybersecurity contractor, you discover a vulnerability in the websites payment processing system, allowing cybercriminals to inject malicious code, stealing sensitive customer payment information during checkout.
Not only did this breach cause financial loss for your customers but has damaged your reputation and trust of customers.
Solution: To prevent this situation, regular security testing could have identified and patched the security flaw before it was exploited by cybercriminals. This proactive approach could have protected customers and the future of your business.
Think about how this scenario parallels the threats within your industry. Do you keep all of your client files in a CRM software? What happens if your network is shut down for one business day? 3 business days?
Vendors are not just partners, but a potential gateway for cyberthreats. By knowing the risks, implementing a process to deal with them, and using a structured onboarding/offboarding process, you can better protect your organization from catastrophe.
Refer to the flow chart below to determine the next step in testing your software. Not in charge of software? Pass this article along to an IT expert in your organization!
This blog was reviewed by Matt Perrotti, a Senior Penetration Tester at Zelvin Security with 20 years of experience as an IT professional in various cybersecurity roles.
For additional education on cybersecurity, check out our event page for monthly webinars!
Dangers of The Dark Web: How to Reduce Your Risk Navigating the Dark Webs: A Clear Guide Beneath the familiar surface of the internet lies a hidden danger: the dark web. This platform poses serious risks to organizations, such…
Tennessee’s Utility District Association (TAUD) is helping its members comply with the state comptroller’s cybersecurity regulations and helping UD’s maintain efficient operations for its customers across the state. Last week, general managers, office managers, board members and commissioners joined together…
Continuous security testing is an essential component of an effective security strategy. In today’s digital landscape, organizations face a constant stream of potential threats and vulnerabilities that can put sensitive data and critical systems at risk. Without continuous security testing,…
It shouldn’t come as a surprise that the healthcare sector is one of the hackers’ favorite targets. And why wouldn’t it be? Patient data and hospital systems are highly valuable, making them perfect for demanding ransom. Any disruption in the…
You may already have a group of Information Technology professionals, and spend money on security tools to alert, detect, and quarantine security anomalies, so why would you even need to spend money on a penetration test? Well, just like any…
- « Previous
- 1
- 2





